Security: Another Phishing Example (plus Apple Junk Mail Bug)
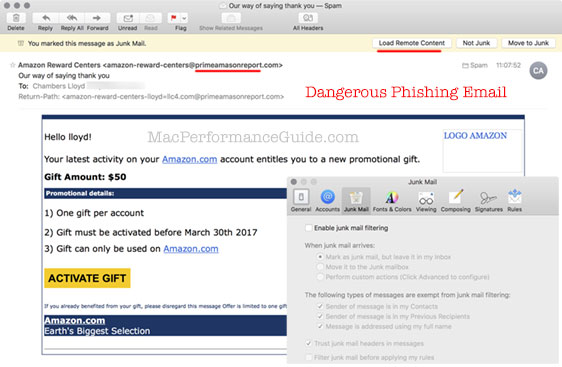
This phishing email (very dangerous) purports to be an Amazon gift award. The idea is that you will click the link, login to a page that looks like Amazon, then the hackers will have your login info to exploit in every possible way, including trying that login on the accounts you might have (which is why one should NEVER use the same login info on multiple sites, certainly not the password, and ideally not the username either).
Continues below with recommended email hygiene.
Secondary issue: the longstanding Apple Mail bug is also seen: junk mail filter is off (as shown), has been off for years, and yet Apple Mail still invokes junk mail filtering. Apple Mail junk mail works in a half-assed sort of way (better than nothing, but barely); I strongly recommend Spam Sieve instead.
Email security hygiene
If the above is not scary enough, here’s a good summary of a gmail phishing approach that is highly effective.
It just amazes me that corporations allow anyone using email to auto-load remote content, or to have links within emails clickable, since both are security hazards. Apple provides for disabling remote content, but has no “disable web links in email” option or option to warn first after running against a highly skeptical pre-flight check (which could even live-test the site for SSL and so on)—shame on Apple, for this is a major security risk vector.
- Always disable loading of remote content by default. Failure to do so gives a ping back to a spammer indicating that the email is a “live one”. You might as well reply stating “thank you, please keep me on your spam list and sell it to everyone you can”.
- Avoid clicking links in emails. This is a major vector for compromising a system. Clicking on links in email should the rare exception. If you really really want to, then right/control click to copy the URL, paste into a plain text empty window and see if the URL looks valid (and is https). If so, then paste it into the web browser. “Yes I’m smart enough” = no one is smart enough. It’s just too easy to make one mistake ever—I’m not. Don’t do it by default. The only exceptions I make are when I am expecting an email and/or for a part I am sure I trust and the headers all look good.
- Have more than one email for sensitive accounts. Do not use an email address for banks, brokerage, or anything sensitive that is the same email as your regular one.
- Use disposable email addresses for shopping, etc. Get rid of them every 3 months or so, moving to a new disposable one. The nasty thing here is so many sites require an email for a login instead of a username—poor security hygiene—making it tempting to use the email address as a username. This defeats the “disposable” idea and it also means an attacker can run that email against thousands of web sites to which you might belong. When possible, use disposable username and emails, to limit the damage. And never use the same password for more than one site—use 1Password to help, possibly leaving out critical logins for financial sites.

 diglloydTools™
diglloydTools™