Using Apple FileVault for Data Security
I worked in encryption for years as an engineer, so I’m not a stranger to it.
All these years have avoided Apple FileVault because of the performance hit. But with the Apple T2 chip in newer Macs such as the Mac mini I am currently testing doing the encryption in real time (no performance hit), I thought I would try it.
See the details of enabling FileVault further below as well as reader comments.
Nerd discussion
After fully configuring the 2018 Mac mini and running a variety of tests (results coming soon), I turned on FileVault.
If FileVault actually encrypts data, I would expect disk I/O reads and writes to occur at maximum speed until the entire 1TB internal SSD is encrypted (or at least the 505GB of data on it). But instead I see no disk I/O at all. Rebooting, I see no disk I/O either.
In other words, FileVault cannot possibly be re-encrypting the data. In other words, all data was encrypted to start with, using a fixed key stored without itself being encrypted by any user-supplied password. Or it was never encrypted and still is not encrypted, but that alternative is too huge a bug to be credible, so I rule that out.
The behavior I observe implies that turning on FileVault and supplying a password does nothing more than encrypt the encryption key already there using the user-supplied password (and presumably a random salt value or vice versa). Because if the data is already encrypted, the decryption key and/or salt value either must remain the same, or all the data must be decrypted and re-encrypted.
Which suggests some level of security risk since that key already existed without the password protection of the user-supplied encryption password. I presume that the T2 secure enclave somehow forestalls this security risk, but I do not know the details. Maybe there is some per-chip specificity that forestalls a general security weakness. Even so, that assumes hardware invulnerability, which is not possible.
The Samsung T5 behaves the same way when enabling encryption, so presumably both Apple and Samsung have a similar approach in that the data is actually always encrypted.
Update 13 Dec: reader Simon N writes:
You might want to look into PDF Apple T2 Security Chip Security Overview for details on how encryption works with the T2 chip. Pages 5 and following should answer your questions.
MPG: works pretty much like my chain of deduction had—very well done, but also guaranteeing total data loss if anything goes wrong—see comments from Jeff H further below.
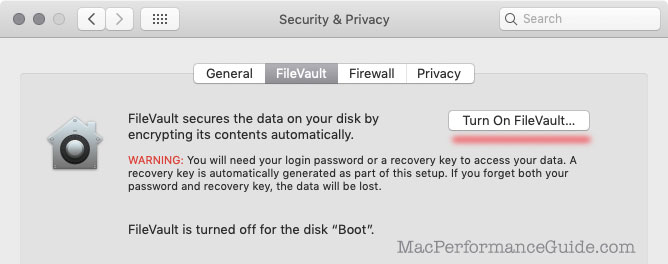
Enabling File Vault
Turn on (or off) FileVault in .
Using iCloud to provide a reset is adding another vector for a security breach. Casual users might find this acceptable, but no serious approach to security would add a new compromise vector.
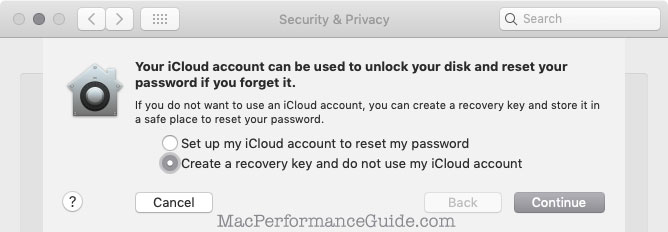
I fail to understand how if I forget my password that I would remember or have on hand the recovery key—might as well just store the password, same as storing a recovery key.
Reader comments on File Vault
Jeff H writes:
I just read your blog post on FileVault on the 2018 Mac mini and wanted to share my horror story of FileVault on the 2018 Mac mini:
Last night, I enabled FileVault on my Mac mini from within System Preferences. This morning, when I booted my Mac after shutting it down, I was prompted to enter my password to sign in, and it didn’t work! After a few incorrect tries, I was prompted to enter my Recovery Key, so I entered my carefully recorded Recovery Key, and that didn’t work either.
So basically I am now completely locked out of my Mac, with no way to recover.
Here’s the crazy thing: if I boot into Recovery Mode (holding cmd-R at boot time) and then try to launch Terminal from within Recovery Mode, I am prompted for my administrator password to open Terminal. If I enter my password there, it works!
So somehow the system installed in Recovery Mode has my correct password, but BridgeOS or EFI or whatever controls the early boot process for volumes with FileVault enabled is borked, so now I am permanently locked out and I’m going to have to restore my entire Mac. :-(
So be very careful with FileVault on the 2018 Mac mini. If you haven’t rebooted yet after turning it on, say your prayers first.
MPG: sad story, both for Jeff and for the one more atrocious and unacceptable tale of Apple Core Rot. As far as can be told, Apple no longer tests software in any reliable/consistent way—edge cases are simply not considered as far as I can tell. I say this based now on five years of inexplicably obviouis problems, often fixed with a ".1", ".2", ".3" update or emergency update all within a month or two of releasing a new macOS version.
Even with Mojave on the Mac mini, Migration Assistant failed (hung) and then had a serious of error messages—a garbage user experience unworthy of a startup, let alone the world’s most successful company.
Barton T writes:
I’m curious about the way the T2 encryption works, in that I have used WD external drives in the past which have hardware encryption. If the drive is removed from the enclosure any of the data on it is toast. Without the original enclosure there is no way to decrypt the data. Needless to say I haven’t used those drives for a long time, although I did pillage the drives from a few of them and use them as a sort of cold archive (in multiples) for some very old data (after reformatting of course).
Is this relevant anyway, since as I understand with soldered on SSD in the newer Macs, if any part of the system dies (SSD, T2, RAM, Processor, etc.) there is no way to recover the data anyway, since they even removed the data recovery port from the latest MBPs. And what does this mean for encrypted data that is backed up to or stored on an external drive — I’m guessing/hoping decryption can be independent of the T2 chip that handled the initial encryption — although now I’m confused about the T2/filevault system anyway after reading your piece.
[followup]...
Yes on those drives the enclosures are doing the encryption. The danger with them was that the disk could only be decrypted by the same enclosure. If the enclosure had a hardware fault you couldn’t put the drive into another WD enclosure of the same type to read the data. Not what I would call backed up data. There was no way to bypass encryption either it just happened by default.I know a few people that use them that have no idea that if something as trivial as the USB port pins getting bent means total data loss. Lucky for me I discovered the problem before it was too late, but it does make me cautious about stuff like the T2/encryption. Thanks for the clarification.
MPG: always backup in triplicate, and with independent devices.
in the described situation, I presume that the enclosure is doing the encryption. So of course the drives are inaccessible without that enclosure. Reformatting is the only solution for re-use.
It is true that if a Mac with a T2 chip dies, data in many cases is gone forever. However, a backup backs-up cleartext (non encrypted) data, so backups are unencrypted (an important point good and bad), unless the backups themselves use some other form of encryption.
The T2 chip can apparently also encrypt data on external drives, but that has to be set up for that drive. More on that later.

 diglloydTools™
diglloydTools™