Beware of Phishing — Fake “Apple Limited”
See previous security tips and previous phishing posts.
Nearly all phishing uses bait (and you’re the fish). Bait can be subtle, threatening or insulting. Don’t bite. All bait is designed to provoke a reaction: fear, anger, an appeal to your innate decency to help with or solve a problem, etc. Appeals to decency and honesty work because most people want to set things right, even if they did not cause the problem—it’s the desire to help.
Don’t let emotions be baited into helping someone hack you.
Below, the attached screen shot shows a relatively crude attack. It is crude in that it does not use Apple graphics, but resorts to incompetence in that it uses crude layout, garish red, and words like “WARNING”. Still, plenty of people get suckered into such things. And if the hackers are competent and use real Apple imagery, the usual Apple fonts and perfect grammar, etc?
NEVER CLICK on LINKS or ATTACHMENTS in EMAILS!!!
Never means never unless you gain the technical competence to verify the email. Even so, that can sometimes take several minutes to be sure—and the more sophisticated the phishing, the easier it is to overlook a crucial detail.
Details on the risks of this particular email further below.
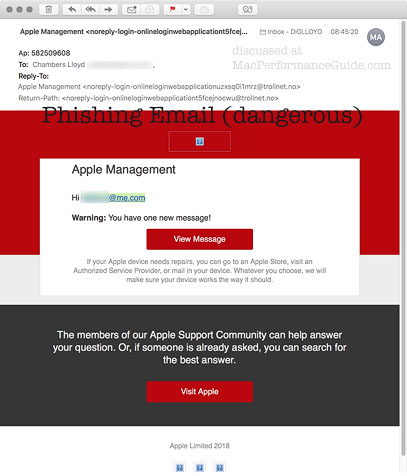
The phishing email in more detail
See Apple Mail Security: Viewing Mail Headers.
There is a red flag right in the mail headers. Do you really want to respond to an email purporting to be from Apple but actually from trollnet.no?
Source code for the ad is base-64 encoded, so that the average user cannot even see what the nasties are. The terminal command 'base64' can be used to decode this incomprehensible encoded content block. Once done, the clickable come-on buttons can be seen to go to these two URLs [a space was added to defeat them as URLs here in this post]:
https //mega.nz/ <== do NOT go here
http //dothemetal.com/403727504.asp <== do NOT go here
It should be obvious that these are not Apple web sites. Land mines are embedded in the content source code, like this for the “View Message” button:
<a id="bottom-button" href="http ://dothemetal.com/403727504.asp" target="_blank" style="...omitted...">View Message</a>

Apple’s sloppy approach in Mail is unacceptable
Why does Apple Mail EVER allow this level of exposure to risk? It is security malfeasance for an email program to present users with such risks.
Safari has active detection of malware sites, but Apple Mail blithely enables outgoing links, making them clickable and thus a serious risk.
It’s about time Apple fixed such sloppy security practices in Apple Mail. Users should not have to be aware of such risks—the risks should be eliminated. We get new emojis with every OS release with top billing in Apple press releases, but Apple cannot be bothered to fix a core Apple Mail security risk? You can’t make this stuff up.
The proper first step that Apple should take is to disable all outgoing links in all emails so they are no longer clickable as links. Bonus points for showing the actual destination URL instead of the title. In terms of security, 99% of users would be well served by this . And would bitch and moan about the loss of convenience, but it is the smart thing to do by default.
Next, allow the user to downgrade the security from there, e.g., allow clickable links to (1) only sites previously visited and (2) known-good sites and (3) enable all sites as is allowed now for those who like to take the risk. A bonus feature would be to change the links so that clicking on one presents a dialog showing the actual destination URL and a rating as to safe, unsafe, unknown, then allow the user to take the risk by choice. I deem this a useful thing for technically skilled users, inadvisable for most.
Why hasn’t Apple fixed this extremely dangerous practice right in Apple Mail, and done it two years ago? My view is that the Apple Mail development team surely has been badly damaged over the past few years, because Apple Mail is rife with bugs.

 diglloydTools™
diglloydTools™