On Ransomware
MPG offers personalized consulting to help you or your business choose and configure a Mac. And/or to design a robust backup strategy for the worst case scenarios.
Just yesterday I wrote about backup reliability and the critical importance of robust backup strategy. Today, all over the news is the worldwide panic about ransomware attacking PCs running Microsoft windows, for example Global Cyberattack Spreads as Experts Try to Limit Damage.
The reporting is awesomely bad in one way: it fails to emphasize that this is yet another in the litany of tens of thousands of Microsoft Windows attacks, dropping the huge context elephant in the room: operating system. I state upfront that macOS is NOT immune to cyberattacks and that threats will grow steadily, but as far as can be told, there is no in-the-wild wildfire malware that has EVER taken down any significant number of Macs via something as nasty as ransomware. Readers, please point me to documented evidence of such an event and its impact and event horizon, if I am incorrect (and Trojans inserted into “free software” don’t count, thieves deserve what they get).
At any rate, one reads little about widespread malware issues with macOS. I mean the Real Deal, stuff that spreads on its own across wide numbers of Macs and does real damage.
And so I ask:
- No business deserves to remain in business that cannot be bothered to execute a backup strategy for customer data and accounting and other critical business data. It is incompetence at the most fundamental level of a business. Failure to maintain offsite backups (NOT on the internet in any way) is the only thing that makes ransomware succeed, because a ransomwared PC can be physically destroyed and replaced if need be, but data is irreplaceable.
- Why in this day and age is ANYONE in a business environment allowed to click on a link in an email? MPG has long advised to NEVER CLICK ON LINKS in emails. Why do mail programs allow this? Why don’t corporations insist on mail software that disables all links and trackers and beacons in emails? If nothing else, require plain text only.
- If someone told you as a business owners that armed thugs would show up at your door and hold all your data for ransom (and if refused, destroy all your computers thus destroying your business), wouldn’t you do something about it, like keep another copy offsite? It’s mind-boggling that ransomware could take down any business. Do businesses go without liability or fire insurance and not pay taxes and so on? How is it even possible that existential risk to critical business data is ignored so that ransomware is more than a nasty nuisance?
- Why does Apple (at the least), still not offer a “disable all external links in emails” option? As well as defeating certain types of encoded spam, misleading headers versus "reply-to", etc? It’s computing malpractice by Apple and everyone else as to where it stands today. There is just no reason for Apple or any other company to sit on its hands while these sorts of attacks happen. And if link-clicking is allowed, why not “sandbox” any browser window started via a link in an email? The level of technology today is so primitive in its failure to take reasonable precautions that it is computing malpractice.
- Why are PC's considered a bargain? It’s one of those jokes in the “bubble” (those in the bubble cannot see out of it): the cost of a system has only marginal relation to the initial cost of the hardware! It’s like saying you can fly coast to coast every month on a $19 ticket but there is a 1 in 3 chance you will die in the next few years due to a plane crash. This is not a good deal by my reckoning. No business in its right mind should be running Windows because it is the #1 target for all types of malware. Maybe Windows 10 qualifies, and maybe it doesn’t, but the reporting I see in the press is pathetic as it does not tackle the key question: how many more PCs than Macs are disastrously compromised each year and year over year, at what economic cost? THAT ought to be the #1 consideration for any sane business person or individual when buying a computer (or even a phone).
- Why is our government (NSA, CIA, FBI, etc) not finding security holes, treating them as national security issues and thus immediately (privately) demanding that companies fix them, rather than exploiting them and thus leaving millions of people and businesses at risk? Isn’t it the first (and only proper) role of government to protect its citizens, including private individuals, businesses, power plants, dams and other infrastructure, all of which of the latter some batch of idiots hooked up to the internet.
- Why are companies with sloppy software practices not held liable for such defects? Car manufacturers that never did have real problems have paid out billions, but software companies get a free pass?
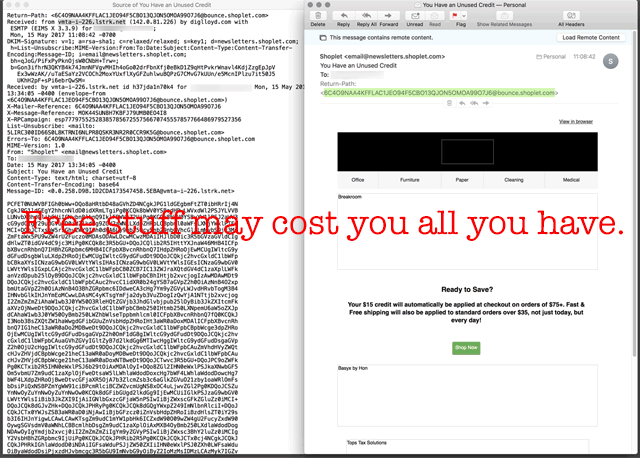
Who knows what this email is below? It is unwanted spam, but non-nefarious? Phishing and dangerous? It looks like one more phishing attempt, and it is base64-encoded (thus hiding its content), so it is almost certainly hiding some nasty stuff. Everyone likes free stuff but why should any business allow its employees to EVER click on links in such an email?
See reader comments that follow below.
David B writes:
As it relates to the ransom ware attacks currently I don't encrypt my own files but if I did would that prevent someone else from being able to do it? Might that be a good defensive measure?
I find myself leaving my externals disconnected, which is really inconvenient but figure it's wiser to turn on the computer and see if there's been an attack before connecting in all my data.
MPG: encrypting your data accomplishes nothing in this context: the malware would encrypt the encrypted files and demand payment in order to decrypt them. Decrypting them would restore the originals, whether they are your own unencrypted or encrypted files.
Leaving local backup drives disconnected or off is some measure of defense as mentioned above. However it is wholly inadequate from a backup perspective: real backups should be stored offsite at a separate location and not connected to the internet in any way (unless it’s a cloud backup and that cloud backup is an adjunct, not a primary backup).
Keep in mind that if cloud backup is automatic malware might encrypt your files, then the cloud backup could replace the unencrypted files with the malware-encrypted files and you would be hosed, making such cloud backup 100% useless. If the cloud backup keeps older versions (the ones not encrypted by the malware), then there is some recourse. If not—bye-bye data.
The foregoing is why MPG has recommendd for many years to keep at least three (3) separate offline backups not connected to the computer or located near it and not on the internet, such as in a safe deposit box. Moreover those backups should NEVER be risked by bringing them all at once to the same site; cycle through them once a week or month. This why having 4/5/6/ copies is ideal; update the oldest backup once a week or so.

 diglloydTools™
diglloydTools™