Apple Core Rot CAUTION: Apple’s macOS Security Infrastructure Might Not be Working on Your Mac (Apple Gatekeeper and Apple MRT)
Apple Gatekeeper is a key component of macOS that does things like checking application signatures (code signing verification, for example). It’s what allows “trusted” applications to run with confidence that they are vetted and safe, e.g., those from the App Store. Apple MRT does malware detection.
There is a dangerous security flaw in Apple’s macOS .
Update Feb 22: the issue persists and the system.log shows some very concerning failures.
I was manually checking my system configuration (macOS 10.13.6) on my 2017 iMac 5K to see that security updates were in place.
I was stunned to find that two critical Apple security areas had not seen an update since December 2017. Specifically, configuration files for Apple Gatekeeper and Apple MRT. That’s nearly 14 months in which I was exposed by out of date configurations.
Checking with an acquaintance, I learned that on his system, configuration for Gatekeeper and MRT had not been applied since July 2018—so his were out of date by 7 months. Which tells me that this is not a one-off issue.
While I follow strict security practices and thus have very low risk, I nonetheless am very concerned that fundamental security infrastructure can enter a state where it does not work. That in itself is a vector for malware!
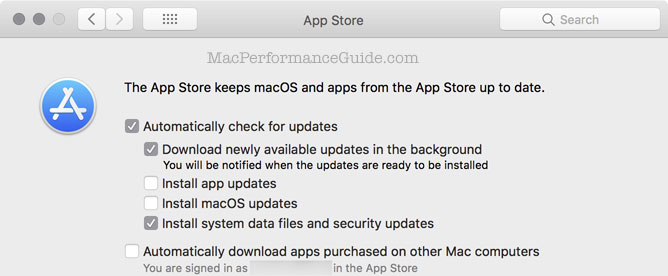
I triple checked all my security settings. Nothing is turned off, nothing is/was set that should prevent security updates from auto-downloading and auto-installing.
The Apple’s Feb 19 security update did NOT fix the issue (nor did any other security update for the past 13 months!). This was the state after Apple’s Feb 19 security update,showing that the update did nothing to update critical infrastructure, or even to detect the problem:
Software Update found the following new or updated software: * macOSInstallerNotification_GM-2.0 macOS Installer Notification (2.0), 1779K [recommended] * GatekeeperConfigData-162 Gatekeeper Configuration Data (162), 3459K [recommended] * MRTConfigData-1.39 MRTConfigData (1.39), 4035K [recommended] * GatekeeperConfigData-140 Gatekeeper Configuration Data (140), 3451K [recommended]
Checking your system
Checking via System Report
Use . As shown below, there were no updates to “Gatekeeper Configuration Data” since Dec 10 2017. Ditto for “MRTConfigData” (not shown).
The Feb 19 file is there only because I fixed the problem manually (screen shot captured after I forced the update manually).

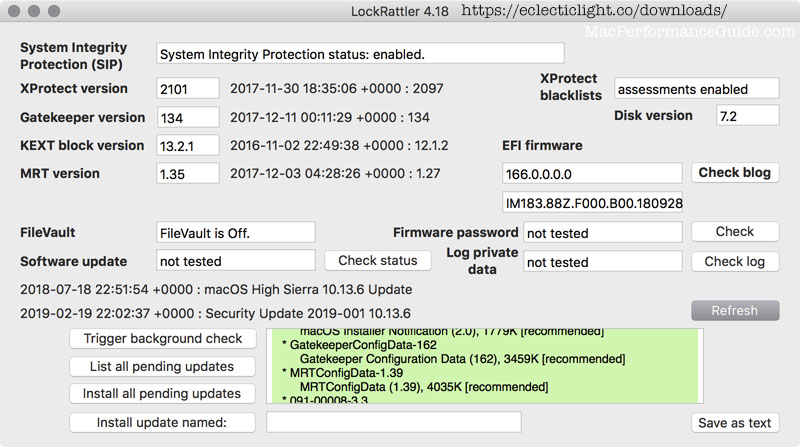
Checking via LockRattler
The most friendly way to check the status of Gatekeeper and MRT and other updates is to download LockRattler at eclecticlight.co.
Below, LockRattler showing my outdated Gatekeeper and MRT configuration status:
Checking and updating at the command line
# check status, should say "No new software available"
softwareupdate --list
# update everything softwareupdate -ia --include-config-data
Critical security infrastructure MUST work
How can this even happen?
- When critical security infrastructure fails to work, this is a priority #0 bug; the reason is unimportant as there are NO EXCUSES for a failure. The infrastructure is essential and there ought to be regular system cross-checks in place to detect such failures, and to warn the user, if nothing else.
- When reinstalling* macOS fails to correct the problem, this is yet another insanely bad bug. Seriously—reinstall and it is still not functioning properly?
- When installing a security update, the update process should verify that all security configuration is up to date. This is yet another bug.
- It is pathetic testament to Apple software (non) quality that a user has to resort to specialty tools and/or command line to fix what should never break in a critical security area.
* Reinstalling over existing system, not erase and install. The install process should ensure a working system and verify all security configuration.
The numerous critical security bugs that Apple has spawned by calendar-driven releases is truly ugly to behold. Add one more.
The fact that the Apple’s security infrastructure can fail in this way with no warning whatsoever is itself a critical bug, because it means that somehow, something can be tweaked to disable updating configuration files for Gatekeeper and MRT—a lovely potential vector for malware!
Curiously, I made this check after applying the Feb 19 macOS 10.13.5 security update. How can you have a security update that does not update security properly?
Even worse, after seeing this issue, I did a reinstall over my existing macOS system and still the Gatekeeper and MRT configuration files stayed stuck at December 2017 versions.

 diglloydTools™
diglloydTools™