macOS HighSierra: New Security Behavior includes a new Zero Day Exploit (kernel level compromise) and Dumping User Passwords
Get iMac 5K at B&H Photo and see my Mac wishlist.
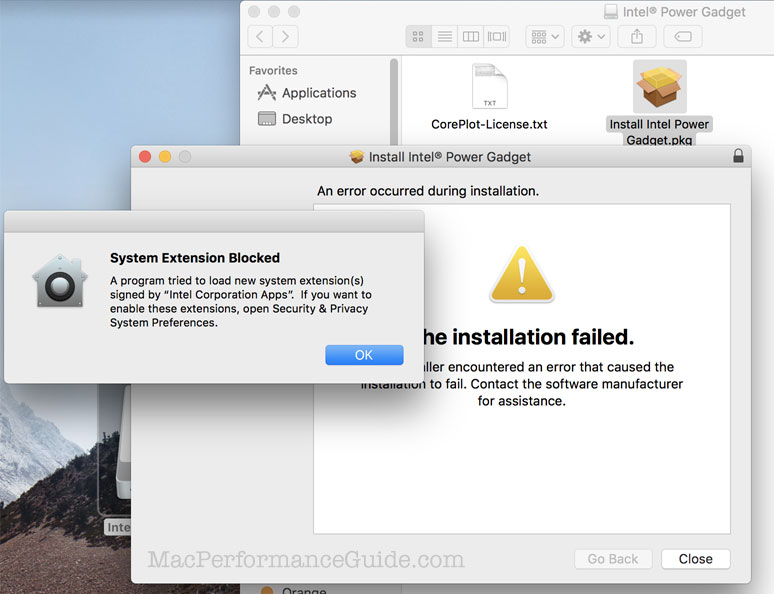
This seems to be a move forward in making macOS less susceptible to malware—good. See Technical Note TN2459 User-Approved Kernel Extension Loading.
...
Update: so much for “good”: there is apparently a zero day exploit that comes with this new security theater. This exploit allows taking full control of the computer, more on that below.
In macOS HighSierra: Brief Use Brings Relief in a Way: Worth Ignoring for a While, I used the term “incompetent” in my post, which is too kind apparently. It should be something like “negligently incompetent”. That is, introducing a new zero day exploit that allows taking over macOS in the course of introducing a new almost marginal useful security feature.
I don’t usually hold developers at fault, since management’s calendar-driven shipping schedule guarantees problems. But in this case I have to make an exception; having worked in security before as an engineering manager (Pretty Good Privacy, startup), our team took everything seriously. You just don’t change Stuff without going over it head to toe, and I’d bet this was rushed out like everything else. Security staff should have the competence to get it right, and the integrity to push back hard against a management willing to endanger user security by rushing out new features.
Zero Day Exploit in macOS High Sierra
So much for “good”:
In brief:
SKEL merely hampers the efforts of the 'good guys' (i.e. 3rd-party macOS developers such as those that design security products). Due to flaws in its implementation, the bad guys (hackers/malware) will likely remain unaffected. While many respected security researchers, system administrators, and macOS developers have voiced this concern, here we'll prove this by demonstrating a 0day vulnerability in SKEL's implementation that decisively bypasses it fully.
...
While at this time I cannot release technical details of the vulnerability, here's a demo of a full SKEL bypass. As can be seen below in the iTerm window below, after dumping the version of the system (High Sierra, beta 9) and showing that SIP is enabled and that kernel extension we aiming to load (LittleSnitch.kext) is not loaded, nor is in the 'kext policy' database, something magic happens. In short, we exploit an implementation vulnerability in SKEL that allows us to load a new unapproved kext, fully programmatically, without any user interaction.
MPG: enjoy your new Mac with smokin' HighSierra.
Dumping user passwords
Here’s another nifty security problem: on High Sierra (unsigned) apps can programmatically dump & exfil keychain (w/ your plaintext passwords) 🍎�😭 v.
OMG OMG OMG OMG OMG OMG

 diglloydTools™
diglloydTools™