Getting Your Devices and Data Over the U.S. Border
Tidits' Geoff Duncan has an excellent article that every international traveler should read:
Getting Your Devices and Data Over the U.S. Border
Imagine a border agent asks you to activate or unlock the device, or provide a code or password to do so? It’s surprisingly common. Maybe the agent wants your Facebook or Twitter password so they can examine everything about your social media presence, not just what’s public. Maybe they want your passwords to WhatsApp, iCloud, Dropbox, or your bank. Maybe these aren’t requests: maybe they’re orders.
Now things get tricky.
- If you agree, border agents can scrutinize and copy your information.
- If you refuse, border agents can seize your devices and even detain you. The CBP cannot refuse to let a U.S. citizen into the country; however, they don’t have to make it easy, quick, or pleasant. The CBP can refuse entry to both foreign nationals and lawful permanent residents. All of this increases pressure to comply.
- If you lie to border agents — “Uh, I forgot my password! That’s not my phone!” — you’ve committed a crime carrying a prison sentence of up to five years.
The last point is perhaps most critical, and far from self evident (at least for that type of lie). Note also that foreign countries may have other laws, more severe and nasty laws, so the key point is to minimize data that is on the laptop or phone or device.
Suggestions, a few ideas to prompt thinking
None of this is legal advice. My own point of view is that the government has no business demanding electronic data particularly the potentially huge damage that revealing a password would cause and its ethical and professional implications, and that the courts are recreant in not recognizing these major distinctions. But that is irrelevant since the law is what it is.
Some of these ideas are simple and relatively easy; others are not worth the hassle for most people. But for those with professional or ethical concerns, they may be worth the bother.
MPG has some suggestions that may be of some worth in defusing the hassle, none of which are dishonest. It’s not your problem to make it easy or obvious, it is only your problem to comply with the law.
As far as I know, Apple does not offer “clean” two-factor login in macOS (username/password + some hardware device), meaning that it ties iCloud to a device (cross contamination in MPG’s view). Still, it may be a good precaution for some. Then the problem would be simple: encrypt the laptop, and leave the device behind (or send ahead) that allows the laptop to be unlocked, it being impossible to unlock it without that device. This ought to be standard-issue for all corporations and government officials, but AFAIK it is not. Problem is, who wants to leave their phone behind? Moreover, SMS messages pop up in plain view.
#0 Disable all auto-login features
This ought to be obvious but perhaps not: do not use any auto-login features in any web browser or anything else! Once logged in, anyone could access all such logins with no effort.
Dispense with multiple kinds of login: do not allow login via iCloud for example; this is tying a computer to an acount, a very bad cross contamination idea that compromises both.
Do not use fingerprint login: use a passcode. You could be physically forced to use your finger—it’s not just the USA and even the USA is hardly a bastion of liberty these days.
#1 Dummy login
This one offers no protection for any computer-savvy person (“ls /Users”), but it might work:
- Create a dummy non-admin account on your laptop—one that looks real but has no sensitive data. Modify a few things so it doesn’t look 100% generic, browse apple.com and a few web sites, add a few innocuous photos to Photos.app, and then leave it alone. Obviously, do not connect to iCloud or similar.
- Enable File Vault (encryption) on the primary login account with sensitive data (the sensitive login account).
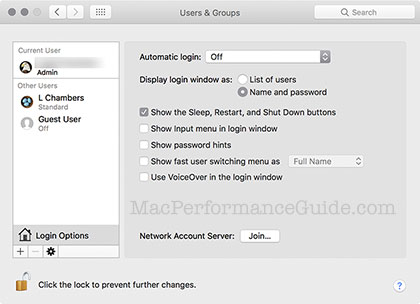
- Set Users & Groups so that it prompts for username and password (so that it does not show accounts to choose from).
If asked to login, login to the dummy account since the “request” is not likely to be more specific than that. That might be enough to satisfy. MPG cannot advise on what to say if asked about the existence of accounts other than what has already been said on not violating the law.
#2 Wipe all free space and extraneous data before traveling
The best approach of all is to not have sensitive data in the first place. If sensitive data is stored in the cloud (Facebook, Google, iCloud), there’s only one step between revealing all that is there—your login. Bad Idea.
- Empty all browser caches and reset all browsers.
- Remove all caches. For command line nerds: sudo rm -rf ~/Library/Caches
- Delete all unnecessary data. If your trip is done and you have the data at home or office, wipe out everything (see next step). A hassle, but it sidesteps the data issue.
- (do this last of all) Wipe all free space before traveling, using for example diglloydTools dgl wipe and wipeFree command.
#3 Get the data off the laptop
You’ll still want to follow the previous suggestions as per caching and wiping. A few ideas:
- Put sensitive data on an encrypted external drive. At the least, it now requires finding and connecting the drive before the “gimme the password” demand is made (never store it or a backup in the same bag as a laptop, sensitive or not). Leaving the connecting cable separate would be one more minor hurdle.
- FedEx data ahead before traveling and/or put it on some obscure place online. Obviously the encryption must be strong and with a strong passphrase.
#4 Password vaults
Users of software like 1Password have a particularly thorny problem: revealing that master password would disclose one’s entire life: logins and all passwords to them, including financial accounts. And the government could retain that data. Very nasty. I would be prepared to forfeit my laptop permanently rather than do so. So it may be wise to not use 1Password for international travel. At the least, take precautions to use a master password that you cannot remember—find some other means—so you can truthfully say you do not know the password to the vault.
Full hassle example: print out a very long and complex password, but leave a chunk of it behind with someone you trust. Upon arrival, they can read you the missing characters. You don’t have the full password, neither do they, nor does an eavesdropper, and you can truthfully say you do not have the full password.
Minimize: create another vault, retaining only the strictly necessary logins and passwords. Do not travel with the full vault.
On the flip side there is a certain protection with 1Password: I can truthfully answer that I do not know the passwords to most of my accounts, since they are buried inside my 1Password vault and are random gibberish. And if I remove the vault before travel, it’s impossible for me to get at the passwords. I could, for example, send a strongly encrypted vault to a friend or co-worker, or put it onto some obscure online service, then download it upon arrival.


 diglloydTools™
diglloydTools™